
Backup & Recovery Solutions in Dubai | Acronis Cyber Protect
Get your business cyber resilient with Al Hutaib's leading Backup and Recovery Dubai solutions. We offer easy, efficient, and secure protection for any workload, minimizing downtime and safeguarding against cyber threats.
Acronis Cyber Protect: The Unified Approach to Business Resilience
Overcoming increasing IT infrastructure complexity and cyberattack sophistication requires a comprehensive backup solution. Acronis Cyber Protect integrates reliable Backup and Recovery Dubai services with advanced anti-ransomware technologies to keep your data safe from any threat. This unified approach eliminates the need to manage separate tools for security and data protection, which simplifies IT management significantly.
At Al Hutaib, we specialize in implementing and managing Acronis Cyber Protect. We ensure your data is protected across more than 30 workloads, including physical, virtual, cloud, and mobile environments. This seamless integration allows for quick, reliable recovery of your applications, systems, and data following any incident, making your business truly cyber resilient.
For organizations needing an advanced continuity plan, Acronis also integrates seamlessly with Disaster Recovery services in Dubai, allowing you to securely spin up full production environments in minutes. This means your business can meet strict recovery SLAs without unexpected costs, which is a major advantage of using unified Acronis Disaster Recovery solutions in Dubai.
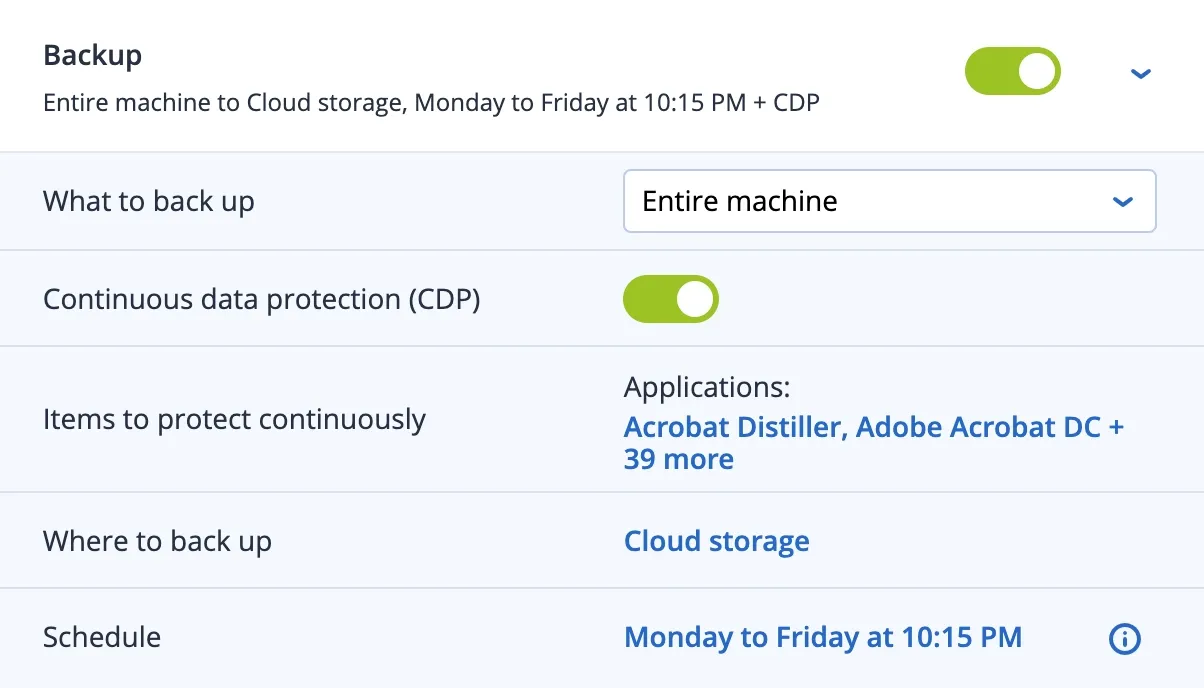
Key Capabilities of Acronis Cyber Protect
This solution provides powerful protection features designed to simplify management and maximize security.
Data Protection Across 30+ Workloads
Acronis Cyber Protect simplifies data protection for over 30 workloads and multi-generational IT. It centralizes the protection of servers, virtual machines, computers, cloud environments, and even mobile devices. Any new application or device is automatically protected, delivering continuous and comprehensive data safety.
Quick, Reliable Recovery
Get fast and reliable recovery of your apps, systems, and data on any device, from any incident. By using a unified backup format, we can easily restore your data to any platform, regardless of the source system, which is crucial for minimizing downtime in Dubai.
Secure Ransomware Protection
Defend your data with built-in ML-based ransomware protection and blockchain notarization. This powerful technology monitors your system in real-time, preventing zero-day threats from encrypting your files.
File and Disk-Image Backup
We provide both File and disk-image backup. You can back up individual files or capture the entire system as a single image file, which facilitates fast bare-metal recovery to dissimilar hardware if required.
Continuous Data Protection (CDP)
Ensure users never lose critical data relating to customizable applications. Acronis’ agent monitors every change made in the listed applications, continuously backing up changes. This guarantees zero data loss.
Drive Health Monitoring
Avoid unpredictable data loss and proactively improve uptime by monitoring drive health. Using machine learning on S.M.A.R.T. reports, Acronis can alert you about a disk issue before it happens, enabling precautionary measures.
Advanced Recovery Technologies for Minimal RTO
Al Hutaib uses Acronis technologies to achieve best-in-industry Recovery Time Objectives (RTOs), getting your business back online in mere seconds, not hours.
Acronis Instant Restore
Reduce recovery times by immediately starting your backup as a Windows or Linux virtual machine directly from storage. Have your VM up and running in mere seconds, while Acronis Instant Restore technology invisibly moves your data to the host in the background.
Acronis Universal Restore
Minimize expensive downtime by restoring Windows and Linux systems to dissimilar hardware, including bare-metal physical, virtual, or cloud environments. By overcoming compatibility issues, Acronis Universal Restore technology ensures quick and easy system migration with a few clicks.
Variable Block-Size Deduplication
Protect more systems while reducing the impact on disk-storage and network capacity by capturing only the blocks with data that has changed since the previous backup. This minimizes storage space by detecting data repetition and storing identical data only once.
Unique Cybersecurity Features Integrated with Backup
Acronis goes beyond simple data retrieval. It ensures that the data you restore is clean, compliant, and ready for action.
Anti-Malware Scanning of Backups
Acronis Cyber Protect ensures that you can always recover malware-free. By centrally scanning your backups for malware, Acronis helps detect and remove threats, ensuring you restore a clean, safe backup every time.
Safe Recovery
Removing detected malware and applying the latest anti-malware definitions during the recovery allows users to restore the OS image safely, reducing the chance of reinfection from a previously compromised image.
Immutable Storage
Ensure the integrity of backup data with immutable storage, preventing alterations or deletions by any unauthorized entity, including ransomware, for a customizable period. This solidifies your defense.
Forensic Data Collection
Simplify future security analysis by collecting digital evidence—like memory dumps and process information—from disk-level backups, which is crucial for compliance and internal investigations.
Why Choose Al Hutaib for Your Backup and Recovery Dubai Needs?
Al Hutaib is your local expert, providing end-to-end management of your Acronis solutions. We ensure correct implementation, local billing, and 24/7 support to maximize your cyber protection investment.
Certified Deployment Experts
Our team holds the highest Acronis certifications. We handle complex migrations (P2V, V2C, etc.) and ensure your implementation uses the best practices for the UAE market.
Local Support and Accountability
You get rapid, localized support from our Dubai team. We provide SLA-backed resolution times and a single point of contact for all your backup and security needs.
Flexible Storage Options
We help you integrate the perfect storage solution, whether it's Acronis Cloud, Microsoft Azure, local NAS, or a hybrid configuration, ensuring you balance cost and compliance.
Transparent Licensing
We manage all your Acronis licensing and provide clear, local billing in AED, simplifying vendor management and ensuring your compliance status is always up to date.
Start Your Journey to Guaranteed Business Continuity
Don't risk your data security. Partner with Al Hutaib for expert Backup and Recovery Dubai solutions powered by Acronis Cyber Protect.
Frequently Asked Questions
What is Acronis Cyber Protect, and how is it different from normal backup?
Acronis Cyber Protect is a unified solution that combines data backup with advanced cybersecurity. Unlike normal backup, it actively scans your backups for malware and uses behavioral AI to stop ransomware in real time, ensuring that the data you recover is completely clean and safe from reinfection.
How does Acronis ensure malware-free data recovery?
Acronis guarantees a malware-free recovery through two unique features: Anti-Malware Scanning of Backups and Safe Recovery. The system scans the backup image itself for threats. If a threat is found, it is removed, and the latest anti-malware definitions are applied during the restore process, reducing the chance of reinfection.
What is the benefit of File and disk-image backup?
The benefit is flexibility and speed. You can choose to back up just individual files, or you can capture a full disk image of your entire system. The disk image allows for a bare-metal recovery, meaning if your computer or server hardware fails completely, you can restore everything—including the operating system, applications, and settings—to new hardware quickly.
What is Variable Block-Size Deduplication?
This is a smart technology that saves you storage space and money. Instead of storing a full copy of a file every time it changes, it only stores the specific data blocks that have been modified. This significantly reduces the size of your backups and minimizes the impact on your network capacity, making your backup process much faster and more efficient.
How does Acronis Instant Restore achieve near-zero downtime?
Acronis Instant Restore reduces recovery time by immediately starting your backup as a virtual machine (VM) directly from the storage location. Your system is up and running in mere seconds while the data is moved invisibly to the host in the background, minimizing the business interruption dramatically.
Can Acronis protect my Microsoft 365 data?
Yes. Acronis provides complete, automated, cloud-to-cloud backup of Microsoft 365, supporting Exchange Online, SharePoint, OneDrive, and Teams. This is essential because Microsoft’s native tools do not cover accidental deletion or advanced ransomware attacks.
What is Immutable Storage, and why is it important for ransomware?
Immutable storage ensures the integrity of your backup data. Once a backup is written, it cannot be altered or deleted by any entity—including malware—for a customizable period. This is the strongest defense against ransomware, guaranteeing that reliable recovery points are always available.
Does the service cover data on mobile devices and cloud platforms?
Yes. Acronis Cyber Protect simplifies data protection across more than 30 workloads, centralizing the protection of physical servers, virtual machines, computers, cloud environments (like Azure/AWS), and mobile devices under one single console.
What is the role of the Data Protection Map?
The Data Protection Map helps ensure compliance by providing a visual and detailed report on where your sensitive data is stored. It automatically classifies important files and alerts you if they are not being backed up, allowing you to quickly secure critical assets.
What is Forensic Data Collection?
Forensic Data Collection, built into Acronis Cyber Protect, simplifies internal and external investigations. It collects digital evidence—such as memory dumps and process information—from disk-level backups, which is necessary for compliance and analyzing how a breach occurred.