
Continuous Vulnerability Assessment Services in Dubai
Get your business cyber resilient with secure backup, natively integrated with AI-powered Endpoint Security and Management. Our Vulnerability Assessment Services drive business efficiency and deliver unmatched protection in the UAE.
47%
ROI with payback in under six months
4x
Faster Recovery Times
100%
Malware Detection Rate
20x
Faster RTO potential
Why Choose Al Hutaib for Vulnerability Assessment in Dubai?
We leverage the industry-leading Acronis Cyber Protect platform to offer complete data protection with integrated security and management. Our solution is designed for unmatched performance and reliability, ensuring your systems remain secure, fast, and operational.
Unmatched Performance & Efficiency
- 100% malware detection rate with zero false positives in independent tests, guaranteeing clean data.
- 4x faster recovery, all delivered with the ease of a single click, minimizing potential downtime costs of $250k per hour.
- 40% faster recovery overall to minimize downtime.
- 50% faster onboarding of new tech employees due to the unified, intuitive platform.
- Tangible financial savings: up to 300% reduced CapEx and 12% reduced OpEx by consolidating solutions.
By choosing Al Hutaib, you are opting for a simplified, powerful solution that boosts team productivity with natively integrated cyber protection controls in a single platform, policy, and agent.
What Our Clients Say About Acronis Cyber Protect
Hear from leaders who have achieved superior cyber resilience and efficiency using our integrated solutions.
"The security aspect with vulnerability scans marked made Acronis the leading choice. And even though the other vendors were able to perform backup and recovery, Acronis did it faster."
"BDR Pharmaceuticals sees tangible financial savings with Acronis Cyber Protect. We achieved 300% reduced CapEx and 12% reduced OpEx."
"With Acronis, we are controlling important data and are no longer dependent on our users. With the Acronis platform in place and the success we have already seen, we are now looking at rolling out other Acronis solutions. We now have more workloads protected with 20x faster RTO."
Integrated Protection: Five Pillars of the Acronis Platform
Our Vulnerability Assessment Services are just one part of a unified suite covering all aspects of modern data security and management.
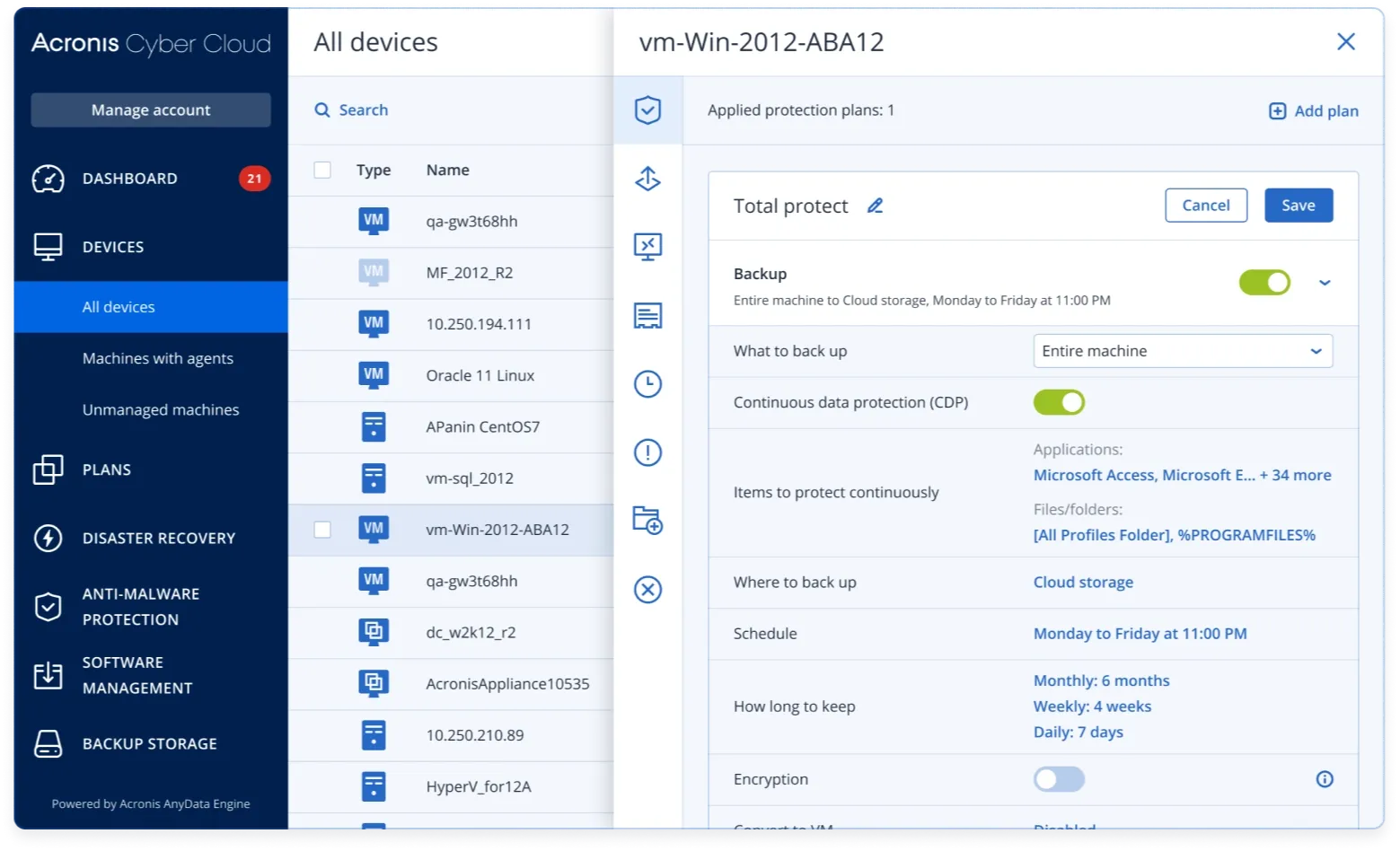
Backup
Cyber resilient backup for physical, virtual, cloud, and mobile environments. Features include: Full-image and file-level backup, Immutable backup, Rapid recovery, Fail-safe patching, and Continuous data protection.
Learn More →Security
Comprehensive defense against evolving cyber threats. Features include: Anti-malware and antivirus, Advanced threat monitoring, Exploit prevention, Vulnerability assessments, and Protection for collaboration tools.
Learn More →Disaster Recovery
Enabling swift recovery from breaches and outages. Features include: Instant failback to VM, Automated recovery across workloads, Failover to safe restore points, and Faster RTOs with runbooks.
Learn More →Endpoint Management
Streamlining IT operations through a unified console. Features include: Vulnerability assessment, Patch management, Software and hardware inventory, Manage workloads with Cyber Scripting, ML-based performance monitoring, and Remote desktop.
Learn More →Email Archiving
Secure and searchable SaaS email archiving for Microsoft 365, designed to maintain compliance. Features include: Microsoft 365 email archiving, Immutable storage, Intuitive web-based console, Audit logging, and Highly secure storage.
Learn More →Achieving Cyber Resilience: The Multi-Layered Approach
We counter advanced cyber threats with Acronis Cyber Protect delivered through a three-layered approach to ensure comprehensive protection, starting with proactive vulnerability scanning.
1. Proactive Layer
Prevention and fortification. Focusing on hardening your environment and preventing attacks before they can cause damage, leveraging integrated management and security features like continuous vulnerability assessment.
2. Active Layer
Real-time protection and continuous monitoring. Providing dynamic, real-time defense and intelligent monitoring to detect and neutralize threats as they occur and prevent downtime. Includes advanced threat monitoring and anti-malware.
3. Reactive Layer
Rapid response and recovery. Ensuring swift incident response and resilient recovery of data and systems after a security event, minimizing business disruption, utilizing features like instant failback and safe restore points.
Flexible Deployment and Broad System Support
Acronis Cyber Protect offers tailored solutions to fit diverse operational requirements, all managed efficiently through its cloud console, supporting hybrid and air-gapped environments.
Cloud Deployment Scenarios
- Small and medium businesses: Get all-in-one protection designed for simplicity and efficiency.
- Microsoft 365 Backup and Archiving: Ensure uninterrupted access and compliance for M365 data.
- Endpoint Detection and Response (EDR): Proactively identify, investigate, and respond to advanced threats.
- Cloud Disaster Recovery: Achieve rapid business continuity with automated failover in the cloud.
Local Deployment (On-Premise)
Acronis Cyber Protect Local enables deployment of a dedicated management server on premises for complete control, rigid data sovereignty, and environments with no or low internet connectivity.
- Sovereign Private Cloud: Meet regulatory compliance by protecting data and infrastructure within your dedicated datacenter.
- Air-gapped Operational Technology: Protect critical data and always-on infrastructure in isolated production facilities.
- Enterprise Edge: Enable secure, self-service backup & one-click recovery for remote worker continuity.
Supported Systems for Comprehensive Coverage
SaaS Apps
Microsoft 365, Google Workspace
Workstation / Mobile
Windows (XP and later), macOS (10.9 and later), Android (7.0 and later), iOS (12.0 and later)
Server
Windows Server, Linux
VM and Cloud
VMware vSphere, Hyper-V, Azure VM, Nutanix, Proxmox, Citrix Hypervisor, Red Hat (RHEV/RHV/oVirt), Oracle LVM, Virtuozzo
Start Your Journey to Guaranteed Cyber Resilience
Don't rely on fragmented security tools. Implement Al Hutaib's expert Vulnerability Assessment Services in Dubai today to achieve guaranteed protection, 20x faster RTOs, and superior security.
Frequently Asked Questions About Vulnerability Assessment
What is the difference between a Vulnerability Assessment and a Penetration Test?
A Vulnerability Assessment uses automated and manual scans to identify security weaknesses (vulnerabilities) and assigns a severity score. A Penetration Test (Pen Test) is a deeper, manual process where security experts actively try to exploit those vulnerabilities to see how far they can get into the system.
How often should I conduct a Vulnerability Assessment?
While traditional assessments are periodic, our service is based on continuous vulnerability assessment, natively built into the Acronis Cyber Protect agent. This ensures that new missing patches or misconfigurations are identified and flagged in real-time, maintaining a continuous proactive security posture.
What is the meaning of "Cyber Resilience"?
Cyber Resilience is the ability of an organization to prepare for, respond to, and recover from cyber attacks. It integrates security (like vulnerability assessment) and data protection (like backup and disaster recovery) to ensure business continuity, even during a major incident.
How does your assessment service lead to faster recovery (RTO)?
By proactively identifying and eliminating vulnerabilities, we prevent attacks that would cause downtime. If an incident does occur, Acronis' natively integrated backup and Disaster Recovery capabilities ensure that recovery is up to 4x faster, with RTOs that can be up to 20x quicker than fragmented, non-integrated solutions.
Does the service cover cloud and mobile environments?
Yes. Acronis Cyber Protect offers secure backup and security features, including threat monitoring and vulnerability checks, across the widest range of systems: physical servers, virtual machines, cloud apps (Microsoft 365, Google Workspace), and mobile devices (iOS, Android).
How does Acronis use AI in its security features?
Acronis uses AI/ML for several security features, including advanced anti-malware detection with a 100% detection rate and near-zero false positives. AI is also used for real-time threat monitoring and behavioral analysis to detect and neutralize zero-day ransomware attacks.